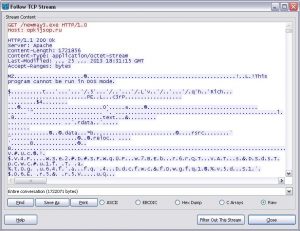
At the next step the decrypted and launched trojan downloader retrieves and executes the next component “newmay3.exe” from the host opkijsop.ru:
This one is downloaded in plain non-encrypted form.
Also I found that other RedKit Java applets are very similar but they use different keys for URL encoding and different AES keys for decrypting EXE payload and classes names are also different. It appears that the RedKit toolkit has a JAR generator that creates a custom JAR from a generic template. Unfortunately I did not have a chance to see this generator yet 🙂