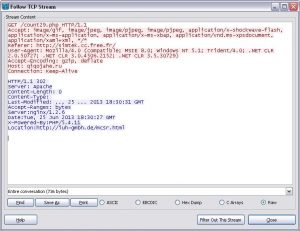
This host just redirects browser to another host iuh-gmbh.de:
Well, this is an actual malware host and now browser starts downloading a Java applet. This one is implemented via JNLP:
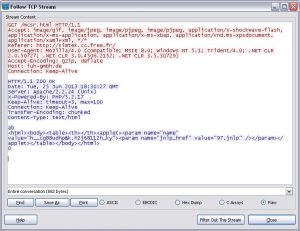
The JNLP specifies which Java applet has to be downloaded and executed and also it provides optional parameters. In this particular case here is the only one parameter with name “value” and actual value is “h__cg88udhp&k.h2j68112h_ky”. Later we will see that is an encoded URL.
The next step – download JNLP file to process it and start an actual Java applet:
Now it instructs the browser to download the applet “67.jar” and execute the Java class “Akula.class”. The parameter was mentioned previously will be passed to the class’s method.